In our previous blog titled Cybersecurity for Beginners we described how to get involved in the cybersecurity community and provided some tips on how to get started in this field. In this post, we will take a closer look at cybersecurity competitions, also known as Capture The Flag (CTF) competitions.
Capture The Flag (CTF) competitions are a type of cybersecurity competition where participants or teams compete to solve various security challenges. These competitions are designed to allow participants to learn and improve their cybersecurity skills while encouraging collaboration and knowledge sharing between participants. CTF competitions provide an excellent opportunity for learning, networking, and improving cybersecurity skills. They are often organised by universities, companies, or groups of interested individuals.
Most CTF events are accessible via the central CTFtime platform, where upcoming events taking place live or online are published. One of the advantages of this platform is the possibility to access the archive, where solutions to tasks from previous competitions are available. These solutions are published by community members or event organisers, enabling readers to improve their knowledge of cybersecurity.
CTF competitions are usually divided into two categories:
1. Jeopardy-style CTF: In this type of cybersecurity competition, participants or teams are presented with various challenges categorized by difficulty. Each challenge is assigned a certain number of points. The higher the number of points, the more difficult the challenge usually is.
Challenge categories in the Jeopardy-style CTF can include:
🕸️Web: The Web category includes online challenges that test your knowledge of how web applications work, common vulnerabilities and misconfigurations. The flag is hidden somewhere in the web application, and is accessed by exploiting logical or technical flaws in the web application. The most common web application vulnerabilities are described in the OWASP Top 10. Web developers have an advantage.
⚙Reversing: The category of reverse engineering is mainly the analysis of devices, programs and processes. Reversing requires a good knowledge of Assembly language and processor architecture. Tools that help to convert an executable file into source code are also essential. After a few hours of reversing, you will only be thinking in 1s and 0s.
📱Mobile: Mobile apps deserve their own category. Most of the time, we’re dealing with Android and iOS apps, which we’re breaking down and studying how they work. The Mobile category is associated with Reversing and Web flaws. For tasks in this category, you will often need rooted phones or emulators.
💥Pwn: The Pwn category first starts with reverse engineering and then continues with writing “malware code” that causes a program to change the way it works or the way the server responds, leading to a takeover of the server and a solution to the task.
🔓Crypto: Cryptographic challenges require knowledge of cryptography and cryptographic algorithms. Breaking algorithms requires a great deal of perseverance and creativity. Mathematicians and logicians are at an advantage. We will start by breaking the enigma.
🔬Stego: Steganography is the science of hiding information in other unhidden messages or files. It involves analysing different types of files in order to discover hidden messages or files within them. This is done with the help of various tools. Sending hidden messages will never be easier.
🛠Hardware: The Hardware category covers knowledge of how electronic circuits, microcontrollers and microprocessors work. It also covers wireless technologies such as Bluetooth, radio signals, Wi-Fi or other protocols. Smart homes will hate you.
🕵OSINT: OSINT stands for open-source intelligence, and challenges in this category you will discover publicly available information. This will make you a professional “stalker”.
🧬Forensics: Tasks that fall under the Forensics category are usually extensive, often analysing files such as hard disk copies, memory contents, etc. It is necessary to put yourself in the shoes of a detective looking for clues about the attackers.
💡Misc: The Miscellaneous category covers challenges that somehow don’t fit into the other categories. Often there are some kind of brainteasers or shorter challenges in this category.
In Jeopardy-style CTF competitions, the team or individual that accumulates the most points within a given time frame is considered the winner. This type of competition is popular because it enables participants to gain and improve cybersecurity skills in a wide range of areas, while encouraging collaboration and knowledge sharing between participants.
2. Attack-Defense CTF: In this type of competition, teams compete to attack and defend servers or services. It is more dynamic and interactive, as participants have to perform attack and defense activities simultaneously in real time. Speed, team preparation and organisation are very important in this type of competition.
In Attack-Defense CTF competitions, each team is provided with its own server (or set of services) that they must defend against attacks from other teams. The team’s objective is to ensure the security and proper functioning of their own services while simultaneously attempting to exploit vulnerabilities in the services of other teams.
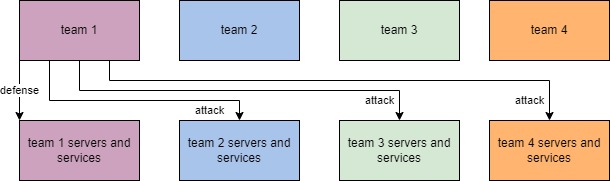
The main features of the Attack-Defense CTF are:
🛡️Defense: Teams must protect their services from attacks by competing teams. This involves vulnerability detection and patching, network traffic monitoring, intrusion detection and prevention, and incident management.
⚔️Attack: Teams must discover and exploit vulnerabilities in the servers or services of other teams to gain access to sensitive data or to disrupt their services. Attack activities include researching, developing custom scripts for automated exploitation of discovered vulnerabilities, and launching attacks.
📊Scoring: Points are awarded based on the success of attacks and defense in each round. Teams earn points for successfully exploiting vulnerabilities of other teams (⚔️ attack) and maintaining the functionality of their own services (🛡️ defense). The team with the most points at the end of the competition wins.
Attack-Defense CTF competitions are a great opportunity to learn practical cybersecurity skills in a real-life environment. Participants need to adapt quickly and collaborate within their teams to effectively attack and defend. This allows the development of skills such as vulnerability analysis, vulnerability exploitation, network management, incident handling, and collaboration between team members.
Where in Slovenia can you take part in CTF competitions?
In Slovenia, various interest groups and companies organize conferences and meetings that also host CTF competitions.
Cyber Night is a very popular event, which sometimes takes place several times a year.

Every year, workshops and competitions are held for aspiring young talents organized within Kibertalent, where they seek young cybersecurity talents to participate in the pan-European competition, European Cybersecurity Challenge (ECSC).

Once a year, the BSides Ljubljana conference takes place, which always includes a CTF competition alongside the lectures. This year, the Attack-Defense CTF competition will also take place at the conference. You can find more information about the event at https://twitter.com/BSidesLjubljana.

