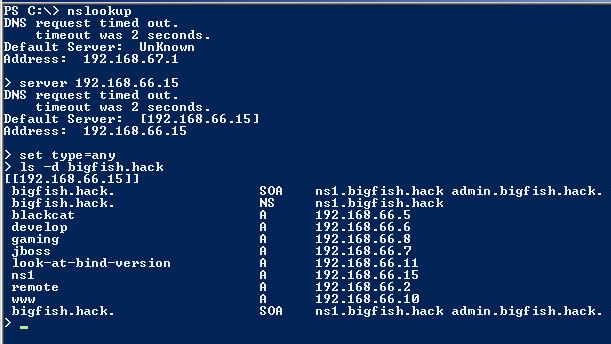
After preparing and organizing some CTF events we discovered that players struggle at a particular task. Often forgotten to look at it, but it is a must-do in every penetration test. We are talking about a misconfigured DNS server that allows zone transfers from any source. This post is not about explaining details of a zone transfer, but rather about how to initiate one in Linux or Windows, and if you want to learn more look DNS zone transfer. Let’s take for example a company named BigFish that owns the domain bigfish.hack. We discovered that on IP address 192.168.66.15 on TCP port 53 is listening a DNS server that resolves domain names for bigfish.hack. To initiate a DNS zone transfer manually from Windows we should use commands in the picture below.
As far as Linux is concerned, dig is our choice. Of course, we could use dnsenum or dnswalk that come by default with Kali Linux, but where is the fun in that. Here is already a oneliner that does the magic with dig.
As we can see, DNS can contain a massive amount of information about a company. Besides domains and IP addresses in use sometimes internal IP addresses are revealed. The other important thing to go from here are virtual hosts. Web servers often host more than one web application. The content of the application is only returned if we address the right virtual host or let’s simplify, enter the right URL address into a web browser.
So next time you should also check DNS for the massive amount of information. Let the DNS be with you!