Here is a short story about access points (AP). We were wardriving through Ljubljana with a mission to analyze the security of Ljubljana’s Wi-Fi network. Our focus was collecting information about different authentication types in use. The goal was to capture a representative set of information about AP’s so that some assumption about the security of Wi-Fi could be given. The only hardware we used was our Android mobile phone with the great Wigle Wifi Wardriving Android application. We already had a large database and we combined it with a smaller one that was obtained fresh from wardriving. The next step was to narrow down the area. Wigle Wifi app stores information about AP’s in a local SQL-lite database, so limiting the area was a piece of cake.
Query bellow was enough.
select * from network where bestlat>45.98 AND bestlat < 46.14 and bestlon>14.42 and bestlon < 14.64 and bestlon > 14.41
The coordinates were chosen approximately so that the urban area was covered in hole. Here are the results.
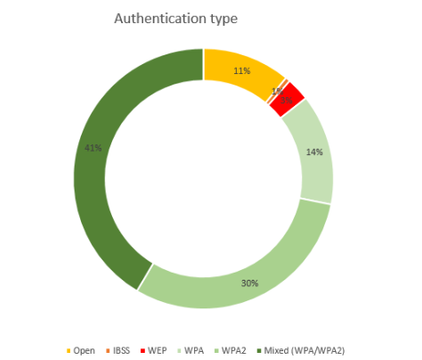
Information about 20263 AP’s was captured. Surprisingly, but from a security perspective encouraging, about 85% percent of AP’s in Ljubljana use WPA, WPA2, or Mixed authentication (WPA or WPA2). But wait a minute, not everything that shines is gold. Approximate 31 percent of these devices have WPS enabled. The implementation of WPS in AP’s is vulnerable to brute force attacks where an attacker can guess the PIN number in a reasonable amount of time. Firmware patches are available for AP’s that make the attack impractical by disabling PIN authentication for some amount of time when consequent invalid PIN’s supplied. But how many users did a firmware update of their device? Probably not a lot. Other vulnerabilities regarding WPS were reported, what makes enabling WPS in general a bad choice?
Also about 14% of AP’s use insecure authentication (forget about IBSS which are most probably ad-hoc networks and are of topic). Why insecure? WEP was long ago and still is considered insecure and OPEN networks are just open. We must consider that the number of networks that were found to be open includes also captive portals which give some degree of protection. But from a hacker’s perspective, captive portals are not so hard to bypass. Techniques like MAC, IP spoofing, and tunneling traffic are well known and don’t require a lot of skills. There are plenty of tutorials and videos in the wild.
The overall state of Wi-Fi security in Ljubljana is not so bad. While there is room for improvement, security awareness is reaching the public or at least the vendors. We should not forget client security. When connected or before connecting to the Wi-Fi network there are plenty attack scenarios, but this is maybe a topic for another blog post.